A number of WordPress sites are currently suffering from a brute force attack, which appears to be driven by a botnet. The attack tries to brute force the username "admin" by trying different passwords from different IP addresses. This renders IP blacklisting ineffective.
Drupal 7 has a feature known as flood control. The user module uses flood control to monitor login attempts, and will block both an IP address and the account after a number of failed login attempts.
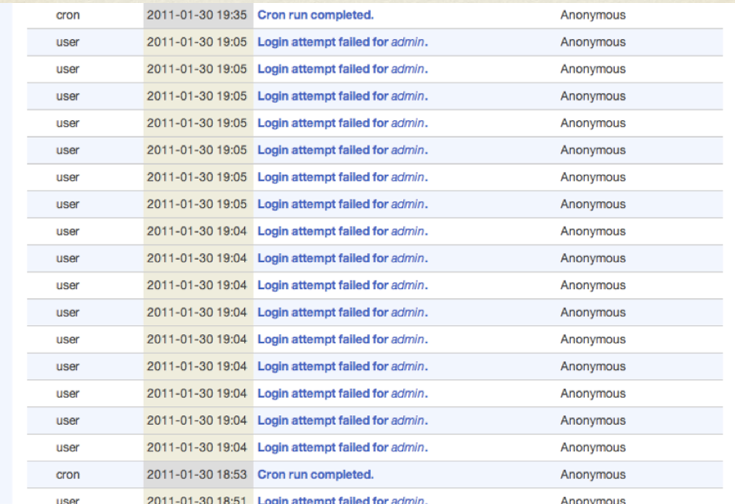
However, out of the box, Drupal 6 is susceptible to brute force attacks. Below is an image of my personal blog getting manually brute forced back in 2011. Unfortunately, (again out of the box) Drupal does not notify site owners when an attack like this occurs.
Mitigation
If you are running a Drupal 6 site, you should consider adding the Login Security module. This module provides flood control like features to Drupal 6, and also allows additional adjustments and features in Drupal 7.
Brute force attacks are more effective against users' weak passwords. The Password Policy module gives site administrators the ability to define complexity requirements for passwords. This can reduce the risk of brute force against accounts on your site.
Also, for an additional layer of security, a number of modules offer the ability to setup two factor authentication. See the Drupal modules for Two-Factor-Authentication wiki page for more information.

Comments
If you have good passwords on
If you have good passwords on the accounts you value, you might actually better off with the brute-force than with login_security and the multi-factor authentication modules.
It is in general wise to limit the reflex to solve a perceived problem by adding yet another module and first investigate trade-offs.
When following the advice, you may be trading potential vulnerabilities for others. Bugs in multi-factor authentication modules can have devastating consequences.
login_security itself also has a number of problems. To quote dstol on IRC: "give me a site with login_security enabled and i can dos it offline with next to no effort".
In summary: I'd hesitate to install any of these modules without doing a very thorough review.
In our last meetup we saw a
In our last meetup we saw a demo of Drupal integration with fail2ban - that will dynamically add the IPs where failed logins are originating for some period of time (e.g. 24 hours).
Since that uses syslog and iptables rather than Drupa DB based blocks, it hsould be a lot less load on the server at least.
Any link for integration with fail2ban
Ok, so there are instructions out there like:
http://www.howtoforge.com/fail2ban_debian_etch
But would be useful if there was some description of how this was integrated with Drupal.
--
OpenConcept | Twitter @mgifford | Drupal Security Guide
Drupal module:
Drupal module: https://drupal.org/project/fail2ban